
None of NSW’s lead cluster agencies have implemented all Essential Eight controls
[ad_1]
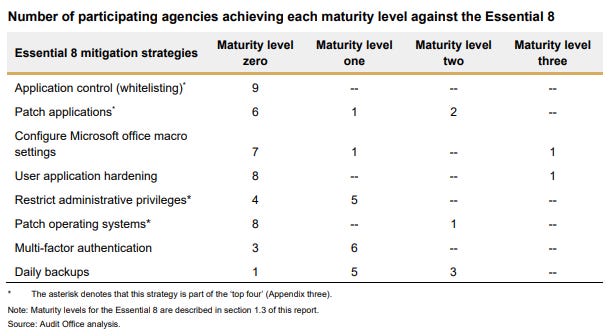
Image: Audit Office of New South Wales
The cybersecurity policy for New South Wales government agencies is not sufficiently robust which is a cause for “significant concern”, according to the state’s auditor-general Margaret Crawford.
“Key elements to strengthen cybersecurity governance, controls, and culture are not sufficiently robust and not consistently applied. There has been insufficient progress to improve cyber security safeguards across NSW government agencies,” the auditor-general wrote in a compliance report [PDF] about the state’s cybersecurity capabilities.
The audit assessed whether nine of the state’s lead cluster agencies — Premier and Cabinet, Communities and Justice, Customer Service, Education, Planning, Regional NSW, Health, Treasury, and Transport — had provided accurate reporting on their level of maturity in implementing the requirements of the state’s cybersecurity policy.
Of these agencies, none of them have implemented all of the Essential Eight controls at level one, with the auditor-general saying that all organisations at a baseline should be at level three.
She added that all agencies failed to reach even level one maturity for at least three of the Essential Eight strategies.
Seven of the nine participating agencies also reported levels of maturity regarding cybersecurity policy and the Essential Eight that were not supported by evidence.
“Each of the nine participating agencies for this audit had overstated their level of maturity against at least one of the 20 mandatory requirements. Seven agencies were not able to provide evidence to support their self-assessed ratings for the Essential Eight controls,” Crawford wrote in the report.
Crawford warned that overstating the effectiveness of an agency’s cybersecurity capabilities could undermine the ability to address cyber risks and ultimately expose them to cyber attacks.
Outside of the nine agencies that received close scrutiny, the data of 95 other state agencies were also reviewed by the auditor-general. In total, of the 104 agencies reviewed in the audit, only five self-assessed that they had implemented all of the mandatory requirements at level three or above. 14 agencies self-assessed that they had implemented each of the Essential Eight controls at level one maturity or higher, while the remainder reported at level zero for implementation of one or more of the Essential Eight controls.
These levels are similar to those reported in 2019 and 2020, with the auditor-general saying better leadership and resourcing would be required if there is to be significant improvement in agency cybersecurity capability.
Crawford said the agencies were not the only ones to blame for this lack of progress, however, criticising the cybersecurity policy itself for allowing agencies to determine what are “mandatory requirements” when addressing cybersecurity risks.
Unlike cybersecurity policies from comparable jurisdictions, the one in NSW lacks a requirement for agency heads to demonstrate reasons for not implementing protocols from the policy. The NSW cybersecurity policy also does not require these considerations to be documented, nor does it require an explicit acknowledgement and acceptance of the residual risk.
There is also currently no requirement for NSW agencies to implement the “top four” controls of the Essential Eight strategies to any designated level of maturity, which are application whitelisting, patching applications, patching operating systems, and restricting administrative privileges.
The auditor-general also expressed concern for the lack of systematised and formal monitoring, by either Cyber Security NSW or another agency, of the adequacy or accuracy of agencies’ cyber self-assessment processes.
Late last year, the NSW audit office found that Service NSW did not effectively handle private information, as a result of the agency experiencing a phishing attack where 47 staff email accounts were compromised. All up, the breach was said to have impacted 186,000 customers and exposed up to 738GB of customer information contained within 3.8 million documents.
Related Coverage
[ad_2]
Source link




